The Fuzzing Project
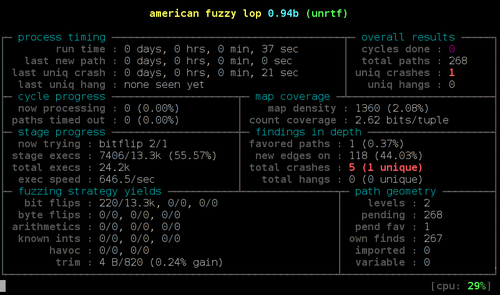
Fuzzing is a powerful strategy to find bugs in software. The idea is quite simple: Generate a large number of randomly malformed inputs for a software to parse and see what happens. If the program crashes then something is likely wrong. While fuzzing is a well-known strategy, it is surprisingly easy to find bugs, often with security implications, in widely used software.
Memory access errors are the errors most likely to be exposed when fuzzing software that is written in C/C++. While they differ in the details (stack overflow, heap overflow, use after free, ...), the core problem is often the same: A software reads or writes to wrong memory locations.
A modern Linux or BSD system ships a large number of basic tools that do some kind of file displaying and parsing. In their current state most of these tools are not suitable for untrusted inputs.
On the other hand we have powerful tools these days that allow us to find and analyze these bugs, notably the fuzzing tool american fuzzy lop and the Address Sanitizer feature of gcc and clang.
The Fuzzing Project is trying to improve the state of things. I maintain some helpful pointers how you can join the effort to improve the state of security in free software.